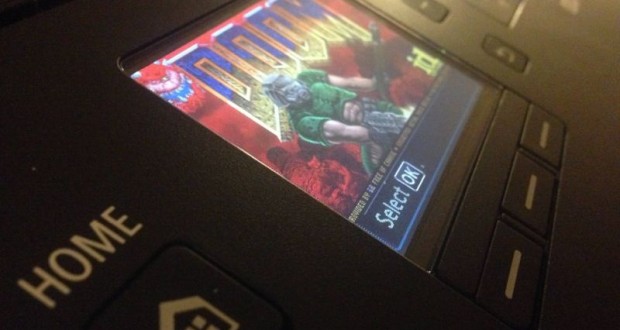
There are many ways to show your programming genius, but few were as satisfying as when security researcher Michael Jordon hacked a Canon printer and got Doom running on the color LCD screen. Since the printer’s screen had roughly the same resolution as the original game it seemed like a great way to test the system’s ability to withstand the hack attempt. It took four months to get the game running on the Canon Pixma printer hardware, but we’d have to say that it was worth it (I know, easy for US to say!) If you’re going to get a Canon printer hacked, why not do it with Doom?
Michael took on the project in order to demonstrate the security issues surrounding devices (like this printer) that combine to form what is now being referred to as the “Internet of things”. As for Canon, the company said that it would patch the discovered loophole(s) on future printers, making them harder to compromise.
How Did He Do It?
Today’s digital printers, like the Canon Pixma, are networked and can be accessed using a web browser for maintenance as well as configuration. What Michael Jordon discovered was that Canon had left open some vulnerabilities to allow access to the device—in particular they had provided no user name or password on the web interface. The problem isn’t that local users could have access, but that, apparently, ANY online user could have access to an unprotected device. Access alone wasn’t an issue, but the interface also allowed firmware updates to the Pixma’s controller software. That’s where things got interesting.
The next steps involved cracking and reverse engineering the encryption used on the firmware. Once that was done, the core computer code was revealed and it was possible for the Canon printer to be “fooled” into accepting new firmware as authentic…even if that “firmware” happened to be the original Doom video game. Since the Canon Pixma uses a 32-bit Arm processor and comes with 10MB of RAM, it was perfectly suitable for running Doom.
Jordan didn’t have to start with scratch. A version of Doom already runs on the Arm processors, so it just took some experimental coding to make it work with the Canon hardware. Fortunately (depending upon how you look at it), Jordan got the code to work just a couple days before he was scheduled to deliver a speech at the UK’s 44Con hacker conference.
If you think you might be susceptible to having your Canon printer hacked, don’t worry. There is no evidence this has actually occurred anywhere else. Canon also has indicated it will “provide a fix as quickly as is feasible”—presumably by adding in standard user names and passwords to current and new printers and issuing firmware updates to all affected models.
Source: BBC.com
 CopierGuide Copier and Multifunction Printer Leases and Reviews
CopierGuide Copier and Multifunction Printer Leases and Reviews